The Veilid Framework
secure, distributed,
anonymous, p2p?
ComfyCon AU 2025
Jim Cheetham / @yojimbo@hackers.town
Jim, unix/network hacker
Federated via @yojimbo@hackers.town
Yojimbosan [RSC] on ComfyCon Discord
$dayjob security for Modica Group, CPaaS
A quick overview :-
We only have 30 minutes ...
- What is Veilid?
- The details, please
- Does this destroy capitalism?
Veilid is not an app
not Signal, Telegram, Tor, IPFS ...
A framework to write and run apps
A protocol to provide a co-operative secure network
A mechanism for storing data on that network
Veilid is ...
designed for mobile devices first, because that's where the users are
therefore expecting high node churn and varied capabilities
very cross-platform; runs on Linux, MacOS, Windows, Android, iOS and WASM
Veilid is ...
a way to break away from the centralised, cost-oriented Internet
a projekt from cDc - the Cult of the Dead Cow,
Medus4 (Katelyn Bowden) & DilDog (Christien Rioux)
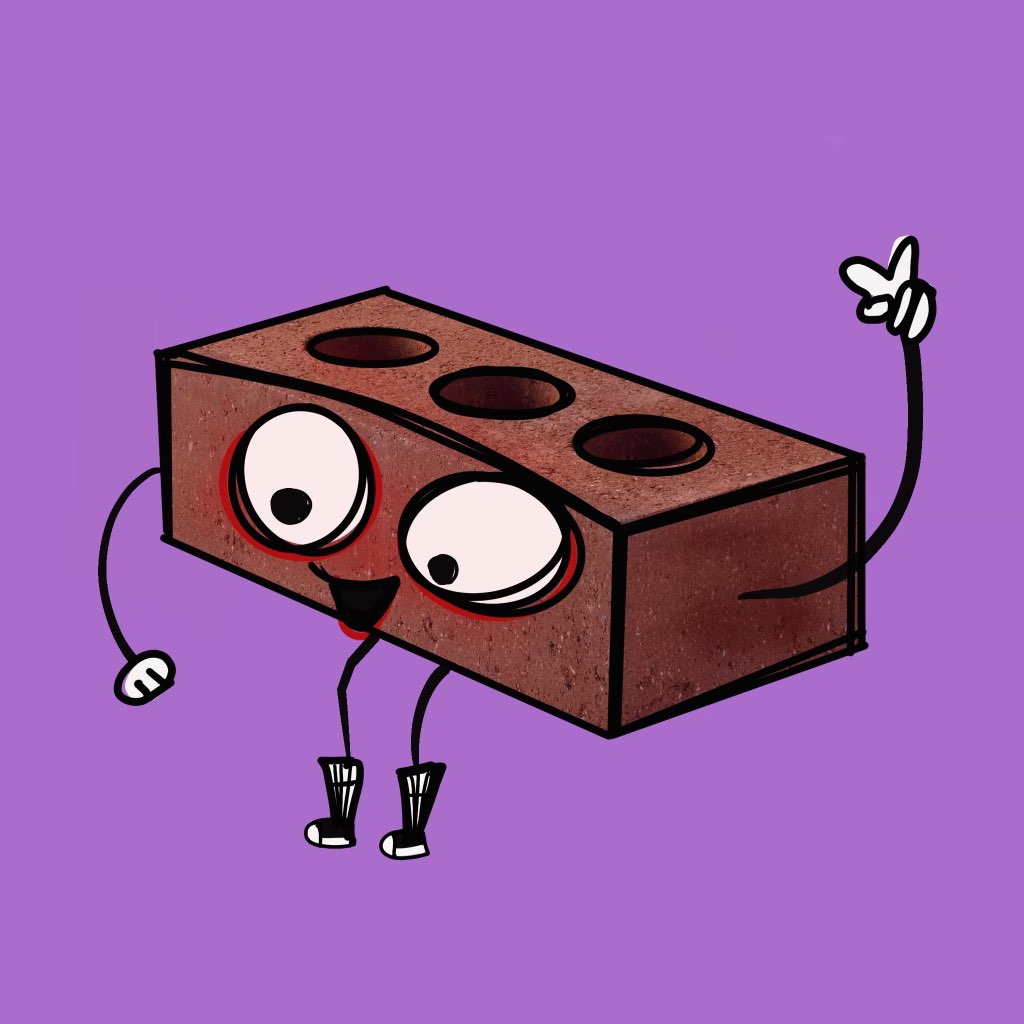
Veilid's mascot is Ellet (he/them), a brick
Because you can build wonderful things with bricks,
they're all basically the same as each other,
and if you throw one at the right place & time ...
Time for some details
- MPL-2.0 Open source code
veilid-corein Rust- FFI+JS plugin for Dart/Flutter
- Python bindings to
veilid-serverAPI
Internet?
Veilid uses the Internet (UDP, TCP, Websockets)
But remains in its own network - no external services, no STUN/TURN, no DNS*
Privacy design guards your IP address
* DNS used for initial node bootstrap only
All bricks are the same
Every Veilid node has the same capabilities
They all store private data securely
They all store shared data securely
They all route data on behalf of each other
They are all unreliable
All nodes are different?
A node's capabilities are measured, not claimed
Data storage is redundant, and refreshes often based on use
Stale/unused data expires over time
Networking!
Nodes don't want to expose their IP addresses
You can communicate directly with other nodes ...
But you can also use "Safety Route" to mask outbound traffic
And a matching "Private Route" for inbound traffic, too
The Veilid Network
Meet Alice & Bob
Traditional direct p2p
Discovery of the 'best' route is implicit,
as is hole-punching, relaying, and STUN/TURN equivalent
BUT IP addresses are exposed between the two
Alice's Safety Route
Bob's Private Route
Maximum Anonymity
Routing Tables - every node tries to know ~256 others
Initial bootstrap via DNS provides ~20, then we ask those for more data
Route discovery to any node will iterate automatically
Data Storage
All nodes, regardless of OS, get the same options
On device :
- ProtectedStore - on-device OS/HW security
Keychain, KeyStore, PStore, SecretService - TableStore - encrypted KV database
SQLite, IndexedDB
Data Storage
On network :
- RecordStore - distributed public data
DHT, encrypted content, subkeys, multi-writer, redundancy and LRU caching - BlockStore - "Coming Soon" for larger data
data sharding and usage constraints
Crypto!
Cryptography
(don't panic)
Versioned Protocol
Rolling upgrades can be used
VLD0 is in use right now
VLD1 is coming to address PQ issues
VLD0:
256 bit keyspaces
- Authentication: Ed25519
- Key Exchange: X25519
- Encryption: XChaCha20-Poly1305
- Message digest: BLAKE3
- Key Derivation: Argon2
What is all this for?
Privacy is a human right
"Social media shouldn't be monetised; Users are not a commodity"
Developers no longer have to monetise their own users, just to pay their cloud bills
Veilid is the technical substrate
Apps
- veilid-server - low impact
- Veilid Chat - PoC
- Intersect - https://github.com/seven-imps/intersect
- vDroplink - https://gitlab.com/bmv437/vdrop.link
- stigmerge - https://github.com/cmars/stigmerge
- Reunicorn - https://github.com/LGro/reunicorn
- Roselite - https://github.com/jdbohrman-tech/roselite
Call to Action!
Run veilid-server on your servers
Join the community via veilid.com
Ask questions, suggest ideas, be thoughtful
Help improve things! Documentation, code, publicity ...
Write an app that uses Veilid rather than a centralised model
Credits
 Cult of the Dead Cow - hacktivism and Veilid itself
Cult of the Dead Cow - hacktivism and Veilid itself

ELLET and Veilid logo from The Veilid project website
 Hackers.Town - support and sanity checking (not a cult)
Hackers.Town - support and sanity checking (not a cult)
 brick by Bernar Novalyi from Noun Project (CC BY 3.0)
brick by Bernar Novalyi from Noun Project (CC BY 3.0)
Slides via revealjs